1. Introduction
The fifth of the six processes devoted to risk management is that of 11.5 Plan Risk Responses. Out of the six processes, five are done during the planning process and the sixth one is done during the course of the project during the monitoring and controlling process.
This fifth process uses several tools to come up with risk responses that are specific to that risk, but before you come up with a specific response, the first step is to come up with a general risk strategy for the risks that you have identified and analyzed in earlier planning processes. That is the subject of this blog post.
2. General Risk Strategies
There are four general strategies for dealing with risk, depending on whether they are negative risks (threats) or positive risks (opportunities). Which strategy to use depends on two factors: the probability of the risk occurring and the impact that it would have on the project if it were to occur. For the sake of simplicity, let’s categorize both the probability and impact of a risk into high and low categories. Then we have the following matrix for negative risks and positive risks:
| Probability | Impact | Strategy (-) | Strategy (+) |
| High | High | Avoid | Exploit |
| Low | High | Transfer | Share |
| High | Low | Mitigate | Enhance |
| Low | Low | Accept | Accept |
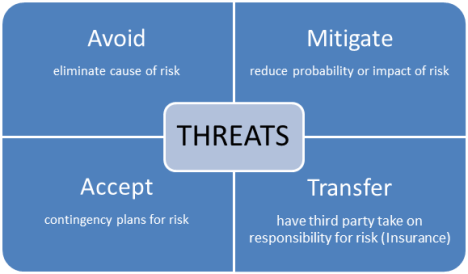
3. Strategies for negative risks or threats
a. Accept
As can be seen, if the risk is low in terms of probability and impact, you can simply accept it. Accepting a risk does not mean ignoring it: risks in these categories that are accepted are put in a watch list. During the course of the project, this watch list should be reviewed to see if the probability and/or impact of the risk has increased.
b. Avoid
On the opposite end of the scale, if the probability and impact are high, you should so all you can to avoid that risk. Some ways of avoiding risk are by clarifying requirements so that the potentially high-risk portions of the scope are excluded, or if the risk is to the schedule, by extending the schedule.
c. Transfer
Now, if the impact is high and the probability is low, you may want to transfer the risk to a third party. Examples in the case of manufacturing would include the purchasing of product liability insurance or, if the risk has to do with a certain component, outsourcing the manufacturing of that component to a company that is better equipped to handle it.
d. Mitigate
A fourth strategy occurs when either the impact or the probability is high, and that is to mitigate the risk by lowering the probability of it occurring, or reducing the impact on the project if it occurs.
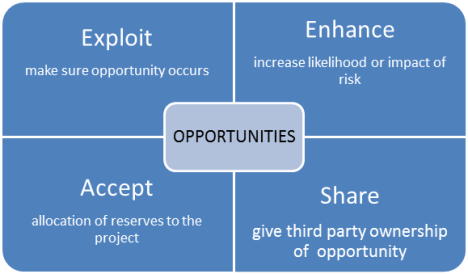
4. Strategies for positive risks or opportunities
Now the “flip side” of negative risks are positive risks are opportunities. Going in parallel order to the explanation of the four risk strategies of negative risks above, you have:
a. Accept
If the probability of an opportunity is low and the impact on the project would be low, then you should not actively pursue it because that would be waste of resources, but rather watch out for it and take advantage of it if it occurs.
b. Exploit
If the probability of an opportunity is high and the positive impact on the project would be high as well, then you should identify and maximize the probability of occurrence of those events that which would trigger an opportunity in order to exploit it. For example, if there would be a significant cost savings for the project to be done early, then it might be worthwhile spending extra resources to do so, provided of course that the extra resources are more than made up by the cost savings.
c. Share
What if you have an opportunity that has low probability of occurring, but would have a high positive impact on the project? In this case you would share the opportunity with a third party that could best capture the opportunity in order to benefit the project. Examples of this include forming risk-sharing partnerships, teams, special-purpose companies or joint ventures.
d. Enhance
If there is an opportunity that has low probability of occurring, then it might be worthwhile to add resources to increase the probability of its occurring.
5. Conclusion
In each case, the idea is to categorize the risk in general terms based on its impact and probability, and then use a general strategy which would be of most benefit to the company. The four general strategies for dealing with risk are based on these two factors, and whether the risk is a positive one (opportunity) or negative one (threat). It is best to memorize these four strategies by considering WHY they are used in terms of impact and probability, and to recognize that the four strategies of dealing with positive risk are mirror images of the strategies of dealing with negative risk.
Filed under: Uncategorized | Leave a comment »

